September 28, 2023
Security in the Age of Digital Transformation
At the recent Fournet Digital Transfomation Summit in London, Fournet's Chief Security Architect, Kevin Prone, led a session exploring how security has had to evolve and adapt as organisations shift into the digital realms.
Starting the session, Prone took the audience on a journey to review the current threat landscape and how attack vectors are emerging. A salient point was made around the current state of global affairs, citing that some organisations can get caught up in not just cybercrime but state-sponsored attacks. This has never been so prevalent during the current global economic crises and conflicts.
Prone also advised that cybercrime remains a prime revenue generator for the criminal fraternity and is, surprisingly, far more profitable than the global drug trade by at least $1.5 trillion. This is why criminal organisations run their cyber units like legitimate organisations."These organisations are not hooded teens in darkened bedrooms, but modern, spacious offices running with management hierarchy, HR, payroll and departments with one aim to make cybercrime more efficient and successful".
The point was also laboured that the attack surfaces we need to protect in our new connected and digital world have expanded exponentially with the perimeter of an ever-changing horizon of moving devices, applications and IoT. This complex environment brings challenges: how do we see over the horizon, and how can we control devices connecting to our networks?
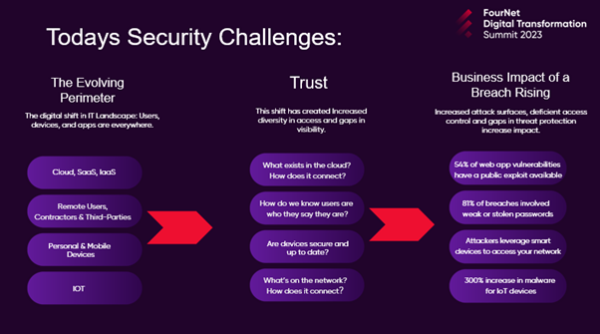
Taking us on a journey through common issues that allow an attack, Prone cited misconfiguration as a common challenge, allowing vulnerabilities to be exposed and exploited. Walking through the Equifax attack, which saw the personal details of 147 million users compromised, this primarily started in an unpatched vulnerability that allowed the attacker to gain access rights to key systems to siphon off personal data. Keeping on vulnerabilities, Prone made the audience aware of the most concerning vulnerabilities, which are not just limited to your network and operations. These included your supply chain, application stack and third-party apps such as MOVEit, which can allow potential intrusion into your systems if not correctly configured or protected.
It was also shown that the common misconception that attackers hit and leave in a small time window is wrong. In fact, hackers can spend ninety-plus days in the network extracting data or other malicious activities.
Criminals for hire and real-world examples
Looking at the Dark Web, Prone told the audience that you can easily procure kits to launch your own ransomware attack or even hire a team to do this for you for a share of the spoils. "It is the success and monetisation of these attacks that keep fuelling the growth, and as more of our personal and work lives are lived out online, this will only perpetuate into the future, increasing risks."
The talk then shifted to two well-known vulnerabilities that affected most organisations, Log4J, which allowed the potential exploit of Apache on 67% of the world’s websites, voice gateways, cloud applications and network infrastructure. He discussed this complexity and how misconfiguration and a failure to release effective, secure patches have become an issue worldwide.
How do we start to firm up security?
It is easy when listening to anyone talk about cyber risks and threats to become overwhelmed and fearful, but there was a focus on a key area that could dramatically reduce the risk profile...Trust.
Prone told the audience, "Trust no one and Nothing" until it has been securely verified and authorised. We can no longer infer trust and must interrogate every access and move across the network. We need to set applicable access rights to provide no network access until endpoint trust is evaluated (authenticate and evaluate system health).
Organisations also need to confine access to essential services through macro and Micro-segmentation and, more importantly, continuously evaluate and isolate threats in real time.
"Visibility is key; you can only defend against what you can see, and many organisations lack the visibility to identify threats at the early stages before these escalate and become a real challenge." Prone
Conclusion
It is clear from many organisations we deal with that they face many common challenges in delivering adequate protection. Resource is a significant issue with teams stretched to capacity, often just keeping the lights on without trawling the hundreds if not thousands of alerts the security stack can fire off. In addition, skills are also a challenge. There is zero unemployment in cyber security due to a lack of skills within the industry. Having teams with the knowledge and expertise to cut through the noise and take remedial steps is crucial but missing in most organisations.
This often results in a massive gap between technology and the human engagement needed to protect the environment that needs to be filled, and the right culture of security by design become a foundation.
FourNet can help.
We have a dedicated security team and 24/7/365 Security Operation Centre that organisations can utilise either as a stand-alone fully managed service or co-managed to act as an extension of your existing team and capabilities to bolster your security posture. Our team instils secure behaviours, constantly tuning and optimising your defences based on our sophisticated threat intelligence and deep experience of defending attacks 24/7
With the advanced SOC and Security Incident and Event Management (SIEM) services we offer and our highly certified and expert team, we can help organisations deliver the ongoing focus, interrogation and defences needed to combat the cyber challenges rising with the move to the new digital age.
Would you like a Measure of your Current Security Posture?
You cannot measure or improve what you cannot see, which is why our Cybersecurity Audit helps to uncover risks and strengths in your security operations and systems. Please call us to arrange your free audit, or click here, and a team member will be in touch.