There have been many news stories and concerns around Chinese technologies allowing vulnerabilities and backdoors for a potential attack, and recently, security researchers have identified over 80,000 CCTV cameras from Chinese manufacturer Hikvision that leave users potentially exposed. Investigations identified a critical command injection flaw within devices that leave them easy to exploit by messages and commands sent to the vulnerable web server.
This flaw (CVE-20210- 36260) was said to be resolved by Hikvision in September 2021, but in a recent White paper published by security specialist CYFIRMA, over 2,300 organisations running thousands of systems and devices have still not applied the necessary security patch.
Knowing these vulnerabilities, cybercriminals continue to exploit the weakness with two known public breaches of the flaw. In addition, in December 2021, a botnet called ‘Moobot’, used the vulnerability to pull systems into swarms to deliver Distributed Denial of Service attacks (DDOs). In addition, The US Cyber security and Infrastructure Security Agency (CISA) published the vulnerability as an actively exploited bug and warned users that attackers could “Take Control” of devices and that remedial action should be taken immediately.
Furthermore, CYFIRMA have said that Russian-speaking hacking forums are openly selling entrance points and relying on the exploitable Hikvision cameras for botnetting or lateral movement.
Additional concerns
Aside from the weakness around commanded injection, there is also a common problem around weak, or default passwords used across devices, with users failing to take adequate steps to strengthen device security. Bleeping Computer reported that it has spotted multiple offerings of lists, some even free, containing credentials for Hikvision camera live video feeds on Clearnet hacking forums.
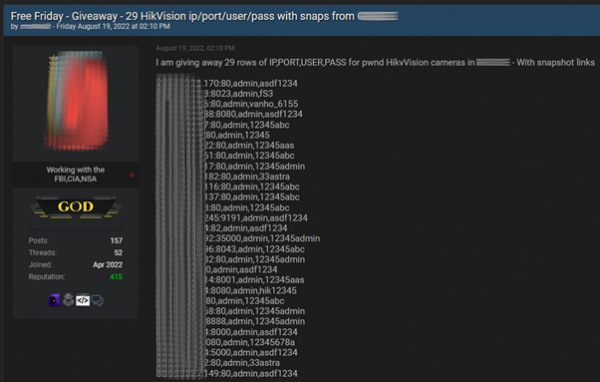
Forum sharing Hikvision hacked endpoints.
What you can do?
There are many calls within the public sector or organisations running high-security operations to look to replace Hikvision within the security portfolio.
One example is the Department for Work and Pensions, which recently confirmed that it will “not be using any security camera equipment manufactured in China”. Hickvision, which the Chinese government partly owns, have also been blacklisted in the U.S as a security risk.
If changing the cameras and systems is not an option, users are advised to ensure that the latest patches and updates are in place to minimise vulnerabilities, review password policy, and isolate the IoT devices from the critical assets using a Firewall or VPN.
If you would like more information about how to secure your operations or look at alternative solutions, talk with our security team, who will be happy to assist you.