
Understanding Government Cybersecurity
Building Cyber Resilience Across the Public Sector
Public sector organisations are under increasing pressure to safeguard digital infrastructure, services, and citizen data. With the rising frequency of cyber threats, this guide explains how the UK’s Cyber Assessment Framework (CAF) helps organisations stay secure, compliant, and resilient.
The Cybersecurity Landscape
Cybersecurity is now a central pillar of operational resilience for public sector organisations, as the risks associated with cyber threats continue to escalate. To address these risks, the UK government has laid out specific requirements for cybersecurity, particularly through guidelines established by the National Cyber Security Centre (NCSC).
One key tool is the Cyber Assessment Framework (CAF), designed to help public sector bodies assess and improve their cybersecurity posture. Here, we explore the fundamental cybersecurity requirements and directives issued by the government, focusing on the CAF's structure and significance.
The Role of the NCSC and Cybersecurity in the Public Sector The NCSC operates as the UK's leading authority on cybersecurity, providing expert guidance, response, and support to mitigate cyber risks across critical sectors. In the public sector, which is a prime target for malicious actors, the NCSC's frameworks help ensure that governmental and public service organisations have robust protection against potential breaches. By adhering to these frameworks, organisations can protect sensitive information, maintain public trust, and ensure continuity of essential services.
What is the Cyber Assessment Framework (CAF)?
The CAF, developed by the NCSC, offers a structured approach to assessing cybersecurity within organisations that play a critical role in the nation's infrastructure.
It is tailored to fit the unique demands of the public sector, covering areas from data protection to resilience and risk management. Its objective is to help organisations identify vulnerabilities, assess risk exposure, and implement effective controls.
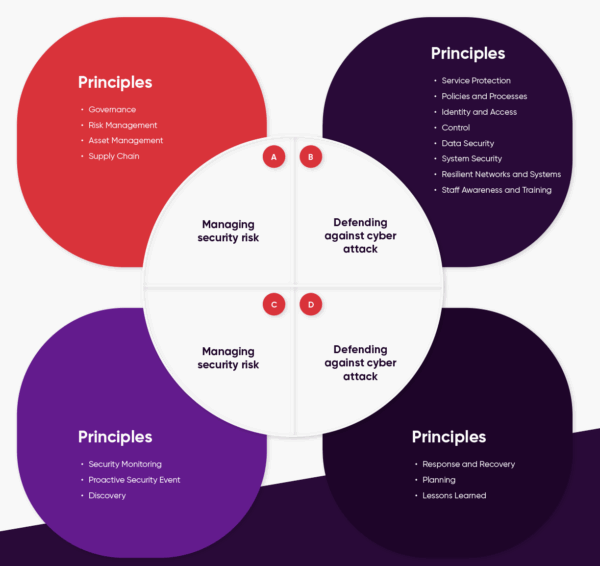
Key Objectives
Managing Security Risk:
Effective cybersecurity begins with understanding and managing risk. Public sector organisations are required to have clear policies and procedures for identifying, assessing, and mitigating cybersecurity risks. This includes regular audits, the establishment of risk ownership, and the implementation of risk management practices throughout the organisation.
Protecting Against Cyber Attack:
The scope of NIS2 is broader, covering a wider range of sectors and organisations. Entities providing digital services, managed service providers, and critical infrastructure operators are now subject to the regulations. This shift means that even organisations indirectly involved in essential sectors must adhere to NIS2's guidelines, extending protection across the supply chain.
Detecting Cybersecurity Events:
Detection is equally vital in cybersecurity. The CAF highlights the need for systems that can effectively identify and log unusual or suspicious activities. These measures ensure that breaches or attempted breaches are recognised quickly, minimising potential damage. Public sector bodies are encouraged to adopt monitoring tools and procedures that can help detect any threat activity within their digital infrastructure.
Minimising the Impact of Incidents:
No cybersecurity measure is entirely infallible, so the CAF requires that public sector organisations have response plans ready in case of an incident. This objective stresses the importance of effective recovery strategies to minimise service disruptions, manage communications, and ensure data recovery if necessary. Having a well-practised incident response plan reduces the potential long-term impact of a cyberattack.
Cybersecurity Directives for Public Sector Compliance
Alongside the CAF, several government directives shape the cybersecurity landscape for the public sector. These are aimed at helping organisations meet their security obligations in line with national security standards:
- Mandatory Security Controls: Public sector organisations are required to follow baseline security controls, which include implementing encryption, two factor authentication, and secure data storage measures.
- Data Protection Regulations: Compliance with data protection regulations, such as the General Data Protection Regulation (GDPR), is essential to safeguard citizen data and ensure privacy. The CAF helps align organisations' cybersecurity practices with these regulations.
- Incident Reporting and Response: Public sector organisations must have a defined process for incident reporting and response. This includes notifying the relevant authorities, stakeholders, and affected individuals in the event of a data breach or cyber incident.
- Regular Audits and Assessments: To maintain compliance, public sector entities are expected to undergo regular cybersecurity assessments, using the CAF as a benchmark. These assessments help identify areas for improvement and ensure that organisations remain aligned with evolving cyber threats.
The Benefits of CAF for Public Sector Organisations
Using the CAF as a guide, public sector organisations can build a robust cybersecurity framework that offers multiple benefits:
- Enhanced Resilience: Public sector organisations are required to follow baseline security controls, which include implementing encryption, two-factor authentication, and secure data storage measures.
- Improved Stakeholder Confidence: Compliance with data protection regulations, such as the General Data Protection Regulation (GDPR), is essential to safeguard citizen data and ensure privacy. The CAF helps align organisations' cybersecurity practices with these regulations.
- Strategic Risk Management: Public sector organisations must have a defined process for incident reporting and response. This includes notifying the relevant authorities, stakeholders, and affected individuals in the event of a data breach or cyber incident.
CAF - Managing Security Risk
Practical Steps for Improving Cyber Resilience
Organisations need to understand cyber risks and their ability to handle and manage a cyber attack. Our consultative approach creates a benchmark of your current security strengths and weaknesses. This allows us to prioritise areas for attention in line with organisational goals and priorities overlayed with risk analysis. Approaching cybersecurity is not just a technical issue, our methodology revolves around three key elements, people, process and technology.
Benefits of Assess for CAF
- Governance: Having visibility into security posture, data, and processes helps meet governance goals. You cannot achieve governance if you don't have a holistic view of IT, Data, Processes, etc. Assess helps provide the insight and intelligence needed to ensure ongoing governance and compliance.
- Risk Management: Fournet Assess provides vulnerability scanning on all external systems protected by your firewall as well as vulnerability testing from inside the network. This report highlights vulnerabilities and areas of risk, benchmarking security posture and allowing for organisations to plan investment and adopt appropriate and proportional security controls.
- Asset Management: Our Assess Service provides a review of your security Infrastructure and network identifying assets that could pose a risk to your security, for example, unpatched devices and those accessing the network that may pose a risk. The Assessment provides a simple-to-understand report detailing strengths and opportunities for improvement and prioritises the most pressing actions first with a traffic light scoring system.
- Supply Chain: By understanding your internal and external network and controls you will have greater visibility of where the organisation interconnects with your supply chain, allowing you to take proactive steps to mitigate risks from these areas.
CAF - Defending against Cyber Attack
- Service Protection Policies and Process: Having visibility into security posture, data, and processes helps meet governance goals. You cannot achieve governance if you don't have a holistic view of IT, Data, Processes, etc. Assess helps provide the insight and intelligence needed to ensure ongoing governance and compliance.
- Identity and Access Control: For many organisations visibility is a key challenge, we can help get full visibility of the network and organisation and help to implement proportional controls for verification and access to systems and applications. We offer a range of services including Zero Trust Network Access (ZTNA) and well as Zero Trust Application Access (ZTAA) fully supported by our 24/7 Security Operations Centre.
- Data Security: We can help protect your data where it resides and whilst in transit as well as implementing access control and backup functionality to protect and restore your data, should the worst happen.
- System Security: From Endpoint to Core, our proactive Security Services will be constantly providing proactive support to protect your network and systems. quickly identifying, remediating and protecting you against threats as they emerge.
- Resilient Networks and Systems: Assess provides a review of your security Infrastructure and network identifying assets that could pose a risk to your security, for example, unpatched devices and those accessing the network that may pose a risk. The Assessment provides a simple-to-understand report detailing strengths and opportunities for improvement and prioritises the most pressing actions first with a traffic light scoring system.
- Staff Awareness training: Your security services are only as strong as your weakest link and humans often fall foul creating serious security incidents. With threats changing your people must be a key focus of any security initiative. We offer a range of services to not only train staff to identify and repel threats, but more importantly to change behaviours to create a culture of security.
About FourNet
FourNet works with some of the most secure, critical and commercially driven organisations in the UK.
Our expertise is in transitioning and integrating complex, legacy systems to deliver the latest communication, collaboration, and contact centre capabilities.
We provide the knowledge and technical expertise to help our customers achieve their digital transformation and customer experience goals. FourNet's Intelligent Managed Service frees up time for our customers to focus on running their business, without having to worry about their communications infrastructure.
How we can Help
FourNet Assess:
Organisations need to understand cyber risks and their ability to handle and manage a cyber attack. Our consultative approach creates a benchmark of your current security strengths and weaknesses. This allows us to prioritise areas for attention in line with organisational goals and priorities overlayed with risk analysis. Approaching cybersecurity not just as technical issue, our methodology revolves around three key elements, people, process and technology.
FourNet Protect:
FourNet Protect provides next generation security services including mail protection, advanced Endpoint Detection and Response (EDR) and Security Access Service Edge (SASE) to protect applications and services. Wherever the network is accessed, and however the perimeter moves, FourNet Protect ensures users are safe and secure.
FourNet Defend:
No matter what technology solutions are in place an attacker only needs to be successful once to compromise the network and organisation. With FourNet Defend our team of experienced cybersecurity professionals work in unison with internal teams, utilising advanced tools and methodologies to swiftly detect, analyse, and mitigate threats.
Defence in Depth: Defence in depth is essential in cybersecurity as it provides multiple layers of protection, reducing the risk of breaches if one layer is compromised. In the UK, where cyber threats are constantly evolving, this layered approach helps organisations detect and respond to attacks more effectively, minimising the impact on business continuity and national security. By combining controls like firewalls, encryption, and access management, defence in depth strengthens overall resilience, fostering greater trust in systems and services.
Delivering a Zero Trust Strategy In today's threat landscape, traditional perimeter-based security is no longer sufficient. Zero Trust is a security model that assumes no trust and requires continuous verification of all entities. This approach significantly reduces the risk of breaches, ensuring robust protection for your sensitive data and systems.
Discover more about ZTNA in our quick guide to Zero Trust

10 Critical Insights for the Evolving Cyber Threat Landscape
Find out More
Understanding Cybersecurity Requirements for CNI and Public Sector
Find out More